Download catalogue of technologies
BinSide: a binary code static analysis tool
BinSide is a static program analysis platform for finding defects in binary code. It is useful when checking programs without source code, such as closed source 3rd party libraries, as well as assisting with required static information to dynamic analysis tools.
Features and advantages
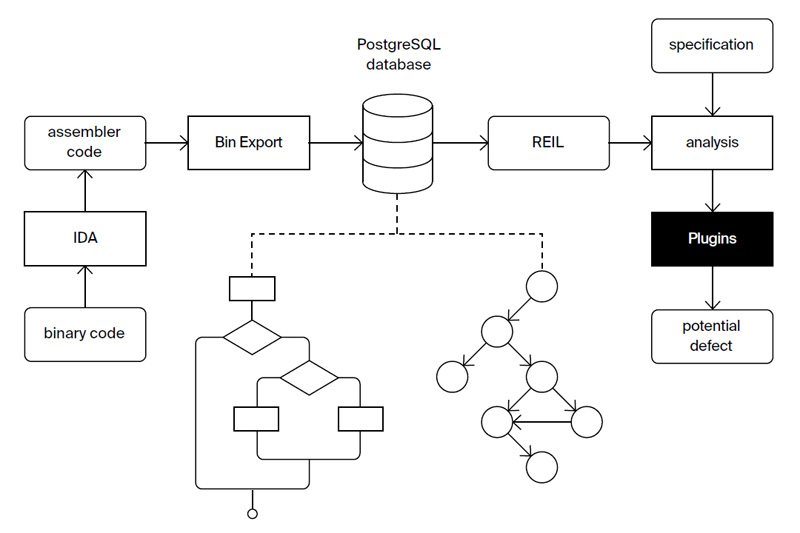
BinSide is a binary code analysis platform based on the BinNavi framework. It translates assembler code into a REIL representation. REIL allows analyzing binary code in a target processor and OS independent way. BinSide provides various analysis types such as defect detection, dynamic analysis optimization, reverse engineering support (via integration with the IDA Pro and Ghidra disassemblers).
BinSide core provides:
- Easy extension:
- individual error detectors are written as plugins;
- the REIL representation of 17 instructions without side effects is used (each assembly instruction is translated into a set of REIL instructions);
- it is possible to specify functions’ semantics to improve analysis quality.
- Supports analyzing executables and libraries for x86-64, ARM and MIPS architectures.
- Detecting the following CWE types: CWE-121 (Stack-based Buffer Overflow), CWE-122 (Heap-based Buffer Overflow), CWE-134 (Use of Externally-Controlled Format String), CWE-415 (Double Free), CWE-416 (Use After Free), CWE-77 (Command Injection).
- An analysis core with the following features:
- Intraprocedural control and dataflow analysis, including value and pointer analysis, taint analysis, tracking dynamic memory, computed jump recovery. The intraprocedural analysis also calculates the function call effect on the calling context and applies call effects for callees;
- Interprocedural analysis and finding interprocedural defects. Each defect has a trace connecting input data and a program point where the defect manifests itself. At this point the analyzer detects a memory model or a security model violation;
- Finding errors on all execution paths (including those not covered by testing or dynamic analysis);
- Displaying defect traces on a source code in a Svace web interface in the presence of debug info in an analyzed executable.
BinSide plugins include:
- A function call effect recovery plugin.
- A plugin for binary code clone search that serves as a base for the following features:
- A plugin for detecting changes between different software versions;
- A plugin for function names markup transfer from one binary file to another.
Who is BinSide target audience?
- Companies that need to check thoroughly the used 3rd party software with no access to its source code.
- Developers who need to increase dynamic analysis quality with the data collected by a static analysis.
- Reverse engineering experts.
- Companies performing software audition or certification.
BinSide workflow
Developer/Participant
Back to the list of technologies of ISP RAS 


